10X Your Password Security
One way to mitigate the risk of a Password breach is to stop using passwords and start using randomly generated passphrases. A passphrase is a combination of words. A good example can be found on the EFF dice words website. For most applications, they suggest using 6 words randomly chosen by rolling 5 dice. Each word has a corresponding combination of 5 numbers from. 1-6. In other words, they are generated by dice(That's D6 dice for all the nerds out there)Here is an example of a strong passphrase that is easy to memorize.
pacifist-area-unfiled-demeaning-rundown-oblivion
It would take a computer about 200 ocrodecillion years to brute force this passphrase so it is highly unlikely to get cracked before the sun goes all supernova.
Here's how it works:
-
Step 1: roll 5 dice
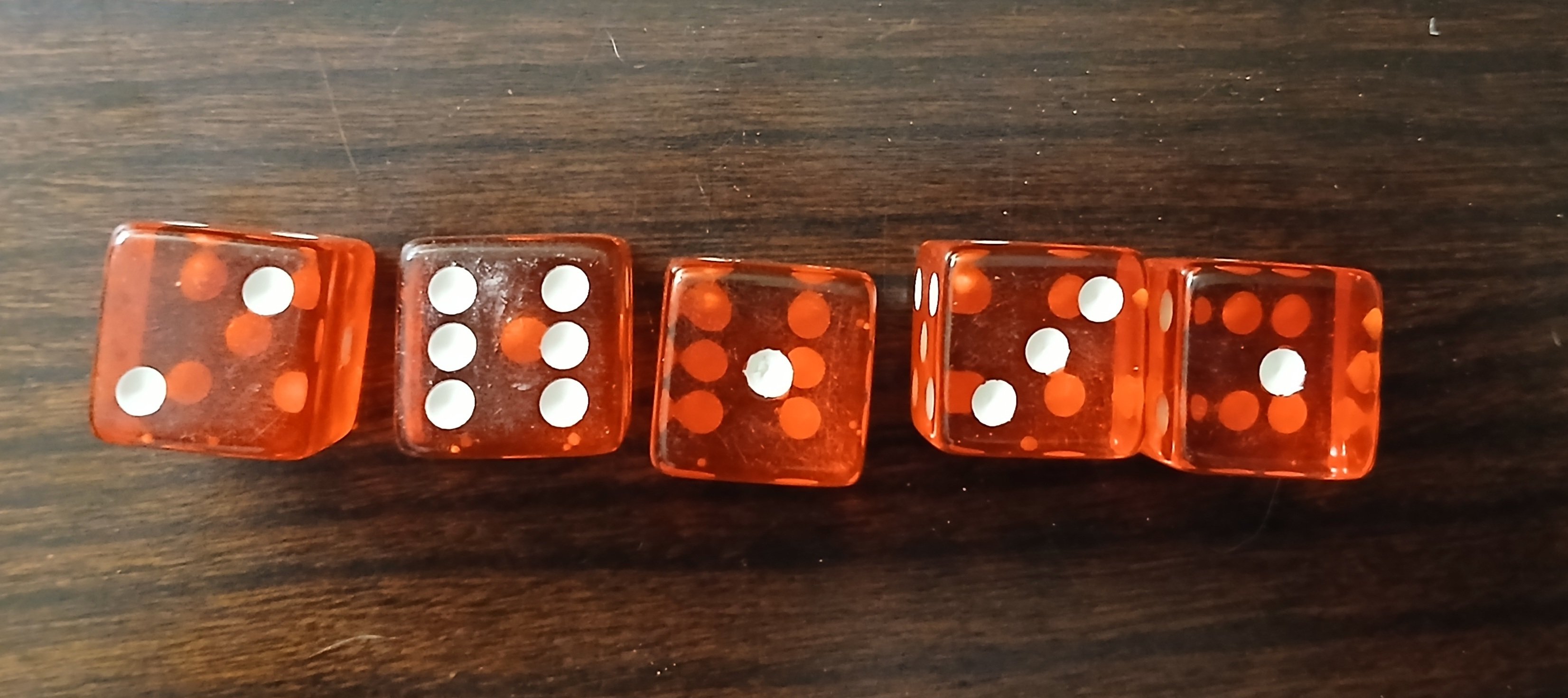
-
Step 2: Find the coresponding word:
In this example, our dice rolls are 2-6-1-3-1 -
Step 3: Find the coresponding word in the eff dice roll list:
-
Repeat this 6 times.
-
Step 4: Write this down on paper. I like waterproof paper made by Rite in the Rain. This is not an affiliate link. I don't make any money off of them. I just like them because they are waterproof and easy to hide. You can also etch the password on military grade steel.
-
Step 5: Use this password password for your passphrase manager like Vaultwarden.
Each character is really a binary number so your passphrase is just a big random number to the computer. This number is hashed with SHA256 or something. If you're really smart, you can calculate this with a pencil and paper, but I use computers and calculators. Xorbin is one of the easier tools, but this can be done in bash using the hash library too. Be aware, typing an actual passphrase you use into any website might be a phishing scam. Don't try to use this for anything you are worried about losing.
Here is the hash we get from the 6 words above:
a41c5312e2957462f9f81597088c1c943c11e864b462cddf49dc55145707b69a
Sweet, Sweet Salt
. If you don't want to hassle with running your own server, bitwarden does the same thing. Last I checked, they only charged $10.00 a year for the premium plan, but it might have changed. They both allow you to:
- Create passwords and passphrases.
- Add special characters, numbers and capital letters.
- Check if your password was pwned.
For example, "password1" was breached 3,339,722 times. If this is your password, you might want to change it.
"Blink-182" was breached 1,810 times. This password would meet most policies. It has a capital letter, special character and a 3 numbers. Where did we go wrong? Blink 182 is a popular punk band. Of course 1,810 people and one hacker thought of this. Think your safe if you change a number? Think again. "Blink-183" was pwned 16 times. Changing the numbers are also not a good idea due to possible dictionary attacks.
I run my VaultWarden using Start9 and it is also available on Umbrel and Yunohost
Let's try our six word passphrase we created earlier.
"pacifist-area-unfiled-demeaning-rundown-oblivion"
This password was not found in any breaches. It should be safe to use. Well...except I put it on the clear net, but you get the idea.
Other Risks
Okay, we have a strong password, but that's not the only threat. A bad guy could trick us with a spear phishing attack or someone installs a keylogger onto our computer. Now what do we do? Be prepared like a boyscout. This is where it's a good idea to use 2fa or two-factor authentication. I like Aegis There are others like Google Authenticator or physical devices like YubiKeys, but I like Aegis becauseyou can create backups. YubiKeys were cool, but this happened and I'm not sure if that's been resolved yet.
Securing your login woth 2fa means one password us an insufficient amount of information to gain access to your account. The attacker would need to pwn the password and your phone to gain access. While not impossible, this is much more difficult.
Here's a Dad joke created by the Duck Duck Go's free AI chatbot.
`Why did the password go to therapy?
Because it was feeling a little "insecure".`
862,887
As Seen on Nostr"
https://habla.news/a/naddr1qvzqqqr4gupzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqdrzvrc94uk7atj94cxzumnwahhyepdwdjkxatjd968jlwzp8r